My Projects Open Source! |
Here you will find an overview of my Software Projects, complete with Feature Lists, Screenshots, and detailed Technical Descriptions. Where applicable, test results and direct links to relevant reference pages are also provided. All my software is developed with a strong focus on 💻Data Security, addressing areas such as:
- Data encryption
- Verification of HASH-based digital signatures
- Secure file deletion
I kindly remind users to utilize these tools 👩💻Responsibly and Ethically. Any unauthorized use for illegal purposes is strictly discouraged. Thank you for your attention and interest in my work!
 |  |  |  | |
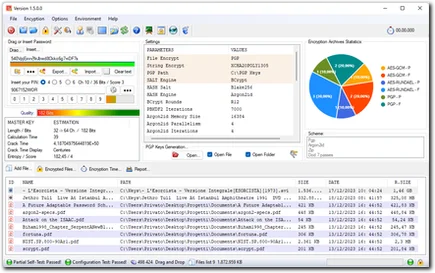
Speedcrypt is a software to encrypt your data that implements some of the most powerful and secure algorithms in the world. It also uses the most sophisticated Password Derivation Techniques, with very robust HASH Functions. Speedcrypt implements libraries such as Bouncy Castle and others among the most used in the world of Cryptography. Speedcrypt is a Free Program for encrypt the files which helps you to manage in a secure way.
The files are encrypted using the best and most Secure Encryption Algorithms currently known:
Speedcrypt is it really Free, more than that: it is Open Source. You can have a look at its full Source Code and check whether the security features are implemented correctly. Following are some of the key features of Speedcrypt:
|
| |
When you download the Speedcrypt Project, you have the option to download four different Packages. You can choose the one that best suits your needs, including the Packages that contain the Source Code. You can review, modify, and recompile them as you wish. Always make sure to download the Speedcrypt Project from the Official Website to ensure that you get completely safe versions, free from viruses, Backdoor and Malicious Software.
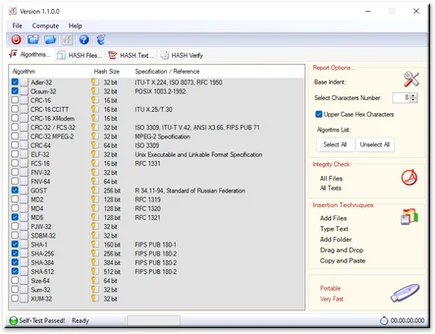
EasyHash is software for generating Digital HASH Signatures that is very simple and intuitive, extremely easy to use, and at the same time highly useful. With this software, you can verify the security of your downloads by comparing the hash signatures generated by the developers of the software you intend to download from the internet. Its ease of use is combined with very high execution speed and a range of options that simplify the user's workflow.
With EasyHash, you can compute hash sums of files and texts. EasyHash supports most of the common hashing and one-way algorithms, including Adler-32, Cksum-32, CRC-16, CRC-16-CCITT, CRC-16-XModem, CRC-32, CRC-32-MPEG2, CRC-64, ELF-32, FCS-16, FNV-32, FNV-64, GOST, MD2, MD4, MD5, PJW-32, SDBM-32, SHA-1, SHA-256, SHA-384, SHA-512, Sum-32, XUM-32 and many more.
I have updated and modified a large part of the EasyHash Project. Now the program is capable of performing HASH verify for files and texts of any origin.
- Ability to select from as many as twenty-five hash algorithms. You can perform targeted selections, multiple selections, or use all algorithms, all with just a few mouse clicks.
- Visualization of Hash reports by indentation of the reports themselves.
- File and text input through various techniques including copy and paste and drag and drop
- Hash verify of files and text through targeted reports
- Fixed minor bugs
- Updated the graphical interface.
- EeasyHash a completely free and Open-Source software distributed under the GNU license. You can freely download the program to use it as you see fit, as well as the Source Code, which you can recompile according to your needs, respecting the license under which it is distributed.
- EeasyHash to function properly in your system requires the .NET Framework 4.8 or higher. You can download it for free from the Microsoft® Homepage: .NET redistributable. The .NET Framework is available for all Windows® Operating Systems, starting with Windows 98. EeasyHash has bin tested on Windows Systems from version 8.0 and later. Unofficial tests were performed on Windows 7 where EeasyHash proved to work perfectly.
If you want to verify the integrity of the downloaded EashyHash Files, you can run the HASH of the files themselves. You can do this on the Internet through appropriate sites or through the HeasyHash Calculator software, which I personally recommend, and check whether the calculated HASH matches the one given on the following Webpage.
 | It doesn't require an Installation Setup and can be conveniently carried on a USB Pen Drive. It doesn't modify the system it operates on in any way and leaves no traces of its presence. You can use it directly from a USB Pen drive, or or to perform local hashing, from the desktop or other locations. | |
SecureDel is a lightweight utility designed to ensure secure file deletion. It features six deletion algorithms that allow you to erase files according to your specific security needs. SecureDel is fast, convenient, and requires no installation. Despite its simplicity, it is a powerful, high-performance tool that enables you to permanently delete all types of files from your hard drive, ensuring they cannot be recovered. The software includes some of the most widely used and trusted deletion algorithms within the developer and security communities. These methods are well-tested and highly effective.
SecureDel is extremely easy to use, featuring a clean, intuitive, and pleasant interface. It can securely wipe files from your hard drive, external storage, or any other supported media, leaving no trace behind.
Throughout its evolution and updated versions, SecureDel has introduced significant improvements, with an even greater focus on user security and privacy. Today, SecureDel can be considered a true Hard Disk Tool, combining secure data deletion with advanced system control capabilities.
Among its most advanced features, SecureDel allows users to independently perform most software repairs on their system. One of its modules integrates all the utilities provided by Windows, offering a comprehensive overview of the available services and procedures within the system.
Key features include:
 Secure File Deletion
Secure File Deletion Detailed System Information
Detailed System Information Network Activity
Network Activity Recycle Bin Control
Recycle Bin Control Clipboard Control
Clipboard Control Active Tasks Monitoring
Active Tasks Monitoring Keyboard and Mouse Activity Tracking [Under complete control of the user!]
Keyboard and Mouse Activity Tracking [Under complete control of the user!] Quick access to all Windows Utilities for System Management and Maintenance
Quick access to all Windows Utilities for System Management and Maintenance
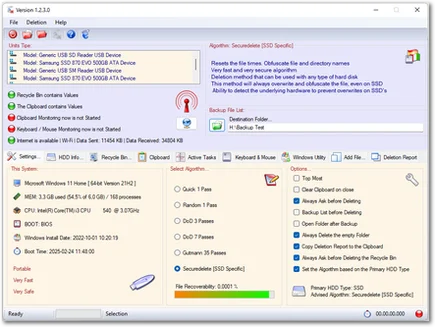
Upon startup, SecureDel provides a detailed Report covering essential system characteristics, Internet Connection Status, and other useful options, including RAM Usage and Critical System Resources.
- The data secure deletion algorithms are six, including DoD 7 Passes used by the United States Department of Defense, Gutman 35 Passes, and Securedelete, the latter specifically designed for all modern hard drives, including SSDs.
- Based on the selected deletion algorithm, SecureDel will display the possibilities for attempting recovery using specialized programs in this field. Additionally, on the main page, the effectiveness of the various algorithms is represented with a pleasant pie chart that translates the aforementioned characteristics into percentages.
- The selection of algorithms is very simple. In the main window, there is a field where you can select the algorithm to use for an operational session with SecureDel. Just click with the mouse, and the selection will immediately become active.
- The program options are also configured in the main window, within a field that can be accessed with the mouse. Each option is very intuitive and easy to activate. When using SecureDel for the first time, the program is already configured for an optimal working session.
- After each deletion process, SecureDel generates a deletion report that will display the following details in order: the algorithm used, the number of files in the list, the size in KB, the time taken, and finally, the date and time of the deletion.The reports can be saved and retrieved whenever deemed necessary. This feature provides an excellent opportunity for users who want to keep their program statistics up-to-date and understand the software's performance across different systems where it is used.
- Upon startup, SecureDel performs a scan of all disk drives, USB drives, or other mass storage devices installed or connected to the system. A detailed report by type and brand will be displayed in the main window.
- A targeted analysis of the hard disks installed in the system will also be performed, with a report displaying their characteristics, including used and available space.
- SecureDel intelligently recommends the most suitable algorithm for secure, fast, and efficient data deletion based on the specific type of hard drives in the system. If the system includes multiple drives with different characteristics, SecureDel will automatically choose the most appropriate algorithm for each individual unit, ensuring optimal performance.
Backup File List:
- SecureDel can prepare a backup of the list of files processed for deletion. Simply enter the destination folder in the appropriate field, enable the related option, and the program will create a backup copy of the data. This procedure is very convenient when you want to sanitize your hard drive and securely store your data on an external mass storage device. Additionally, the backup process ensures that no critical files are permanently lost, giving you extra peace of mind during sensitive operations.
- Since version 1.2.2, when preparing a list of files for the deletion process, SecureDel performs a scan to ensure that the files are not in use by another process. If they are, the program will terminate the ongoing process, freeing the file so that the deletion can proceed without errors and with maximum speed.
- The Drag and Drop functionality has been significantly enhanced and upgraded. It is now possible to drag multiple files and folders simultaneously. With a single selection, you can drag all the files and folders you wish to include in the deletion process directly into the list.
- SecureDel now offers full control over the Windows Recycle Bin. You can view, manage, and even repair the Recycle Bin directly from within the application. This ensures that users can detect and fix any issues or corruption in the Recycle Bin, improving the overall functionality of the system. Whether it's recovering files or verifying if deleted files are properly stored in the Recycle Bin, this feature helps maintain a clean and efficient system.
- It is now possible to securely delete files and folders located in the Recycle Bin. SecureDel integrates seamlessly, allowing the program's secure deletion algorithms to be applied to these items. Additionally, traditional deletion methods are available, although they are strongly discouraged unless the files or folders have no significant value in terms of privacy.
- It is now possible to display the SID of the Windows Recycle Bin and send it to the Clipboard. Additionally, the hidden folder can be viewed. This is very useful for seeing the actual condition of the Recycle Bin: it often happens that files deleted in a traditional way do not appear in the visible folder, but are still present in the real folder. This indicates a malfunction which SecureDel can repair through a specific procedure accessible from the Popup Menu.
- Now SecureDel offer the Clipboard Monitoring: with Clipboard Monitoring, SecureDel allows you to track every change in the Windows Clipboard in real-time. This feature is particularly useful for detecting any unauthorized or unexpected activities involving the Clipboard, such as malicious programs attempting to copy sensitive data without your knowledge. SecureDel provides a detailed view of Clipboard contents, giving users more control and visibility over their system’s operations.
- SecureDel has been significantly improved in terms of graphic adaptation. The program now adjusts to most of the graphic cards available on the market today. The interface remains clean, pleasant, and performs well on most of the resolutions commonly used in Windows environments.
- I created SecureDel as a small utility to be used quickly on any Windows system or from external storage devices like USB drives and others. Now, it's time to further enrich this program with features like Keys shortcuts, offering a fully keyboard-controllable main menu.
In version 1.2.3 of SecureDel, further significant improvements have been made to provide a more advanced and intuitive user experience.
- SecureDel now monitors all storage devices in real time, automatically detecting the insertion of new devices such as external hard drives and USB sticks. This ensures an immediate update of the available drives list, providing more accurate and timely control.
- The user interface has been improved with new icons that clearly and intuitively represent the status of storage devices. This allows for quick identification of connected devices and better file management.
- Thanks to these optimizations, SecureDel becomes even more efficient in monitoring and managing storage units, offering an increasingly seamless and comprehensive user experience.
- Once launched, SecureDel displays a panel containing key information about the operating system, such as the version, RAM usage, processor details, boot type, installation date, and the time since the last system reboot. Additionally, it detects the type of internet connection, and if active, displays the data transmission in KB.
- In this version, a window displaying active tasks has been added, allowing direct interaction with running programs in the system. This feature is particularly useful for monitoring and closing unresponsive applications, discovering the installation folder of programs, obtaining online information for each running task, and copying the task name to the Clipboard for further analysis. All these operations can be accessed via a convenient context menu.
- SecureDel now provides full monitoring of mouse movements and keystrokes. The service can only be activated or deactivated by the user, and once activated, a message will be displayed to confirm that monitoring has started. Additionally, an icon will always be visible on the system taskbar to keep the user informed of the ongoing monitoring.
 Note: This is not a keylogger and only works with the user's explicit consent. It does not create files or logs secretly to send to hidden servers. You can verify the source code yourself—SecureDel is a completely legal, clean program, without any malicious modules or code. If I had intended to create a keylogger, I would have made SecureDel invisible. Additionally, I kindly ask anyone who downloads the Source Code not to create a keylogger for illegal purposes! SecureDel is designed with user privacy in mind, and its Open-Source nature ensures complete transparency. Feel free to inspect the code and verify its integrity yourself.
Note: This is not a keylogger and only works with the user's explicit consent. It does not create files or logs secretly to send to hidden servers. You can verify the source code yourself—SecureDel is a completely legal, clean program, without any malicious modules or code. If I had intended to create a keylogger, I would have made SecureDel invisible. Additionally, I kindly ask anyone who downloads the Source Code not to create a keylogger for illegal purposes! SecureDel is designed with user privacy in mind, and its Open-Source nature ensures complete transparency. Feel free to inspect the code and verify its integrity yourself.
- SecureDel, during keyboard and mouse monitoring, creates and saves a .TXT file in the following location:C:\Users\Your PC\AppData\Local\Temp\ with the filename SecureDel LogSession.txt.At any time, you can check it yourself by following the indicated path. This file will be deleted when the user decides to do so. You can also review the source code to verify that this is the only file created for keyboard and mouse monitoring sessions.
 Note: if you want to monitor the keyboard and mouse even on programs that have administrator privileges, you can launch SecureDel in this mode: right-click on the program icon and then left-click on the Run as Administrator option. The control will be extended to every application.Finally, use the keyboard and mouse monitoring exclusively for the purpose of ensuring that these devices are functioning properly within your system, to monitor your operational sessions, and to track the activities you perform. This feature should not be used for any purpose outside the boundaries of legality or ethical use of my project. It is designed to be a tool for transparency and accountability, not for misuse. I trust that all users will respect the intentions behind this project, which are rooted in promoting security, productivity, and privacy. Any violation of these principles would not only undermine the project's goals but also compromise the integrity of its use. Thank you for your understanding and responsible use!
Note: if you want to monitor the keyboard and mouse even on programs that have administrator privileges, you can launch SecureDel in this mode: right-click on the program icon and then left-click on the Run as Administrator option. The control will be extended to every application.Finally, use the keyboard and mouse monitoring exclusively for the purpose of ensuring that these devices are functioning properly within your system, to monitor your operational sessions, and to track the activities you perform. This feature should not be used for any purpose outside the boundaries of legality or ethical use of my project. It is designed to be a tool for transparency and accountability, not for misuse. I trust that all users will respect the intentions behind this project, which are rooted in promoting security, productivity, and privacy. Any violation of these principles would not only undermine the project's goals but also compromise the integrity of its use. Thank you for your understanding and responsible use!
- The project now allows users to independently repair any issues with their operating system. A new module called Windows Utility has been introduced, providing quick access to all the most important built-in system utilities, along with dedicated Windows maintenance procedures. Essentially, SecureDel consolidates all the necessary tools for system repair, maintenance, and updates into a single module. You no longer need to call a technician—SecureDel lets you handle everything on your own.
- I firmly believe that PC users should have free access to tools that enable them to manage and maintain their software independently. Understanding how a system works not only allows users to perform maintenance and repairs on their own but also contributes to the spread of collective knowledge, fostering a community of more aware and capable users.Seeking professional assistance should only be necessary in cases of critical software anomalies or hardware failures. For all routine maintenance tasks, it is essential that users can rely on their own skills. A more educated and informed user base leads to a reduced dependency on external services, a more efficient use of resources, and overall better system management.This is precisely why I developed the Windows Utility module—providing essential tools that empower as many users as possible to develop their technical skills and take full control of their computing environment. Technology should not be a barrier, but an opportunity for growth and empowerment.Using this software is not just about technical support—it is also an opportunity to uncover the secrets of your system and ensure it remains efficient and high-performing at all times.
- Enhanced the Drag and Drop algorithm and multi-selection.
- Enhanced the file selection algorithm for files engaged in other processes.
- Enhanced the Windows Recycle Bin monitoring algorithm: all events are reflected in real time.
- Enhanced the graphical adaptation algorithm. Now, SecureDel adapts to any graphics card and monitor.
- Enhanced the overall data flow with exceptions that stabilize the program and provide the user with full control over SecureDel.
- Enhanced the deletion algorithms for folders and files within the Recycle Bin. SecureDel now minimizes the margin of error caused by system attribute files and folders as much as possible.
- Minor bugs identified and fixed, of no relevance to the correct functioning of the program.
- SecureDel is a completely free and Open-Source software distributed under the GNU license. You can freely download the program to use it as you see fit, as well as the Source Code, which you can recompile according to your needs, respecting the license under which it is distributed.
- SecureDel to function properly in your system requires the .NET Framework 4.8 or higher. You can download it for free from the Microsoft® Homepage: .NET redistributable. The .NET Framework is available for all Windows® Operating Systems, starting with Windows 98. SecureDel has bin tested on Windows Systems from version 8.0 and later. Unofficial tests were performed on Windows 7 where SecureDel proved to work perfectly.
Below, among the many software tested to try to recover data deleted with SecureDel, a list of some of the most well-known and reputable ones:
Tests performed on:  SATA [HDD] SSD [SSDs] With OS
SATA [HDD] SSD [SSDs] With OS  Windows 7 [No Official Test] Windows 8 - 8.1 - 10 Windows 11 OS Build [22000 - 22621 - 22631 - 26100]
Windows 7 [No Official Test] Windows 8 - 8.1 - 10 Windows 11 OS Build [22000 - 22621 - 22631 - 26100]
Recuva | HDD - SSDs | DoD 7 Passes - Gutman 35 Passes - Securedelete | |
R-Studio | HDD - SSDs | DoD 7 Passes - Gutman 35 Passes - Securedelete | |
Disk Drill | HDD - SSDs | DoD 7 Passes - Gutman 35 Passes - Securedelete | |
DiskDigger | HDD - SSDs | DoD 7 Passes - Gutman 35 Passes - Securedelete | |
DM Disk Editor | HDD - SSDs | DoD 7 Passes - Gutman 35 Passes - Securedelete | |
Stellar Data Recovery | HDD - SSDs | DoD 7 Passes - Gutman 35 Passes - Securedelete | |
Prosoft Data Rescue 5 | HDD - SSDs | DoD 7 Passes - Gutman 35 Passes - Securedelete | |
EaseUS Data Recovery Wizard | HDD - SSDs | DoD 7 Passes - Gutman 35 Passes - Securedelete | |
MiniTool Power Data Recovery | HDD - SSDs | DoD 7 Passes - Gutman 35 Passes - Securedelete |
In order to facilitate the potential recovery of data deleted with SecureDel, all tests were conducted on clean systems, with the various operating systems freshly installed and compatible with the program. The result was that not a single piece of deleted data was recovered. If you have conducted any tests or plan to do so in the future, feel free to contact me for the results obtained. Thank you!
 | It doesn't require an Installation Setup and can be conveniently carried on a USB Pen Drive. It doesn't modify the system it operates on in any way and leaves no traces of its presence. You can use it directly from a USB Pen drive, or for local deletions, from the desktop or other locations. | |