My Algorithms... Algorithms, Classes, Libraries |
On this section of the site, I share the algorithms, classes, and libraries I have designed to provide solid and effective solutions in the fields of data security and other key areas of computing. Each project is released with full source code, a clear usage license, thorough technical documentation, and practical examples to support integration and use. This is an open invitation to developers and enthusiasts alike to benefit from these tools, improve upon them, or simply draw inspiration.
|  | |
I am pleased to present to the Developer Community my Secure Data Deletion Algorithm, named Custom Erase. This system allows users to define a custom sequence of overwrite operations — including Zero writes, One writes, Random bytes, and other techniques — offering maximum flexibility in permanently erasing information. Its goal is to ensure that deleted data becomes completely unrecoverable, in accordance with the highest security standards. The algorithm is easy to interface with, simple, and readily integrable into existing projects, its logic is modular to support further extension.
The Custom Erase Algorithm is a secure file deletion method designed to minimize the risk of data recovery after deletion. It follows a customizable multi-pass overwrite pattern, aimed at erasing magnetic or electronic traces of data on both HDDs and, to a limited extent, SSD storage devices.
- Primary Goal: Prevent forensic data recovery.
- Target Media: Optimized for HDDs; partially effective on SSDs.
- Use Case: End-user data sanitization, secure deletion tools, file shredders.
public static List<string> GetSuggestedAlgorithm() { return new List<string> { "Random", "Zero(0x00)", "One(0xFF)", "Random", "Random" }; } | ||
Total Passes: 5
- Pass Composition:
- 3x Random Overwrites
- 1x Overwrite with 0x00 (Zero)
- 1x Overwrite with 0xFF (One)
This sequence was selected to balance performance, entropy, and overwrite strength. If the user opts to request a suggestion for the most effective sequence, the algorithm will automatically apply the recommended configuration described above. The recommended sequence has also yielded good results in tests conducted on SSD storage devices!
Pass Type Byte Pattern Description:
Zeros | 0x00 | Clears each byte to zero |
Ones | 0xFF | Sets each byte to binary one |
Random | RNG bytes | Cryptographically random bytes |
Each pass type contributes differently to data Obscuration, with Random offering the highest resistance to recovery.
A dynamic evaluation class (
CustomPassEvaluator) assigns a strength score [0–20] based on the selected sequence. The algorithm is evaluated by:- Variety of pass types
- Number of Random overwrites
- Avoidance of weak or repetitive patterns
0–4 | Weak | Low security, easily recoverable |
5-8 | Moderate | Medium security, reduced but present recovery risk |
9-14 | Strong | High security, recovery is difficult |
15–20 | Very Strong | Maximum security, recovery nearly impossible (progress bar shows 100%) |
The strength of an erase sequence lies not only in the number of passes, but in their diversity and unpredictability. Even a few carefully chosen overwrites can achieve near-zero recovery potential when guided by sound logic and precision.
Strength Level Estimated Recovery Chance:
Weak | >40% |
Moderate | ~15–30% |
Strong | ~5–10% |
Very Strong | <5% |
The Default Algorithm falls into the Very Strong Category, with an estimated recovery chance below 5% on magnetic media.
On SSDs, overwrite techniques are less effective due to internal block remapping and wear leveling. These limitations on SSDs are inherent to the hardware architecture and affect all overwrite-based erasure tools — not just Custom Erase. For critical sanitization, refer to NIST 800-88 Guidelines or manufacturer tools supporting ATA Secure Erase or NVMe Format NVM commands.
As for our tests and other:
- Use the default 5-Pass Sequence, unless specific compliance requires otherwise.
- Increasing the number of passes beyond 7–10 offers diminishing returns and can increase disk wear.
- Do not rely solely on software overwrite methods for SSDs if full sanitization or compliance is required.
CustomErase may support partial compliance with:
- GDPR – Data Destruction Requirements
- HIPAA – Secure data disposal
- NIST SP 800-88 Rev.1 – Guidelines for media sanitization (partial)
This algorithm was carefully designed and tested with a focus on practical irrecoverability, while maintaining solid performance. The goal is not theoretical perfection — but real-world untraceability!
In this section, we’ll take a closer look at the internal structure of my Secure Deletion Algorithm and show how easily it can be integrated into your own project, whether you're building a personal tool or a professional application.
The Custom Erase Algorithm is organized into three Main Classes, each responsible for a specific component of the secure deletion pipeline. The architecture is modular, clearly separating pass suggestion, evaluation logic, and execution. This design improves testability, maintainability, and configurability.
The CustomEraser Class represents the core of the Secure Deletion Algorithm. It serves as the primary engine responsible for overwriting data to prevent any possibility of recovery. It is designed for maximum flexibility and can be integrated into both standalone applications and modular architectures using DLLs. Its optimized structure ensures high performance and ease of use, enabling seamless integration into a wide range of software environments.
The algorithm follows a structured and robust procedure:
- Verifying the existence and accessibility of the file before the operation.
- Removing any protected attributes such as read-only, hidden, or system to allow overwriting.
- Renaming the file with a random name to reduce traces of the original filename in the file system logs.
- Opening the file exclusively to prevent concurrent access.
- Fully overwriting the file in 8KB Blocks using a customizable sequence of passes with Zero, One, or Random data.
- Flushing each pass to physical disk to ensure data is actually written to the device and not just cached.
- Truncating the file to zero length at the end to remove any residual content.
- Permanently deleting the file from the disk.
The implementation supports cooperative cancellation through cancellation tokens, providing a safe and managed way to interrupt the process if needed. This modular and optimized approach offers a balanced solution between security, performance, and ease of integration.
Purpose:
Evaluates the strength of a given overwrite pass sequence expressed as strings.
Responsibilities:
- Converts a sequence of descriptive strings into enumerated pass types (CustomPassType)
- Calculates a numeric score based on the type, count, and diversity of the passes
- Assigns a qualitative label (e.g., Weak, Strong) and a visual percentage value for UI representation.
- Penalizes sequences that are too uniform or dominated by weak patterns
- Rewards sequences with strong passes and diverse pass types
Purpose:
Provides a predefined and balanced overwrite Pass Sequence.
Responsibilities:
- Returns a static list of passes considered secure for data erasure.
- Supplies the sequence in textual form, ready to be parsed and evaluated by other components
- Acts as an initial reference or fallback when no custom sequence is specified by the user
As previously explained, I’ve designed my Deletion Algorithm so that it can be integrated into a traditional project or encapsulated within a DLL. For the latter option, I’m also providing the full Source Code, allowing you to review its contents and recompile it yourself if desired. Below, we’ll look at how to use Custom Erase through its native DLL.
First, after creating a new project in the Visual Studio Development Environment, simply download the CustomerEraser.dll and place it in your project folder.
Next, right-click on your project name and select Add > Reference. In the window that appears, browse to your project directory and locate the DLL. Import it and confirm the operation. At this point, you're ready to use my secure erase algorithm.
To fully leverage the potential of my Secure Deletion Algorithm, it's important that your project includes the following components:
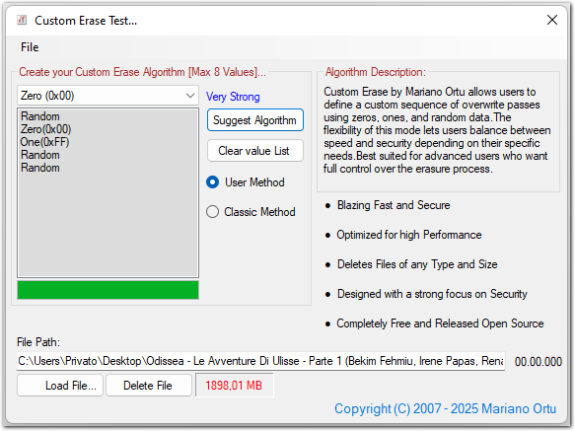
- A ComboBox to load the overwrite patterns used in the customizable erase algorithm — specifically: Zero (0x00), One (0xFF), and Random. These are essential.
- A ListBox to list the selected overwrite patterns in the desired sequence
- A Label to display a numerical score or rating reflecting the effectiveness of the current sequence. This provides the user with immediate, clear feedback on how robust the selected overwrite configuration is — whether suggested by the algorithm or manually created.
- A ProgressBar to visually represent the strength and effectiveness of the chosen erase sequence
- At least three basicButtons:
- A TextBox to display the full path of the file to be securely erased
- Two CheckBoxes to choose between:
- Classic Mode – uses the recommended default sequence.
- User Mode – allows full customization of the erase sequence.
Naturally, you can adapt the layout and interface of the window according to your specific needs, integrating any additional options you find useful. For reference, you may download the sample application I created, named Custom Test, which is also distributed with full Source Code.
We now have everything we need, so let’s see how to make the Custom Erase Algorithm work within our project. Let’s start by declaring a boolean variable and setting its initial value to false:
private bool _SUCC = false;
This variable interacts directly with the core class of my algorithm and enables, with just four lines of code, the entire workflow that handles the success or failure of the file deletion process. Maximum result with minimum effort!
Now it’s time to create the procedure that allows us to utilize the values the user enters into the ListBox, in order to define a customized and effective overwrite sequence. This sequence serves as a valid alternative to the default one provided by the algorithm — which is already optimized for secure deletion, but can be further enhanced and tailored to specific user needs. By allowing users to build their own sequence, we not only provide flexibility but also empower advanced users to fine-tune the deletion process based on their own criteria or security policies. This level of customization ensures that the algorithm remains both powerful and adaptable, striking a perfect balance between ease of use and technical depth. Below is the procedure called CallCustomEraseFromListBox:
void CallCustomEraseFromListBox() { // Retrieve the file path from the input textbox. string filePath = txtFilepathdel.Text; // Validate the file path: check for null/empty and file existence. if (string.IsNullOrWhiteSpace(filePath) || !File.Exists(filePath)) { MessageBox.Show("Invalid file path.", "Custom Erase Test", MessageBoxButtons.OK, MessageBoxIcon.Error); return; } // Initialize a list to hold the selected custom pass sequence. List<CustomPassType> passSequence = new List<CustomPassType>(); // Parse each item in the custom pass list and add it to the sequence if valid. foreach (var item in listCustom.Items) { if (Enum.TryParse(item.ToString(), true, out CustomPassType pass)) passSequence.Add(pass); } // If no valid pass types were selected, show a warning and exit. if (passSequence.Count == 0) { MessageBox.Show("No custom pass selected.", "Custom Erase Test", MessageBoxButtons.OK, MessageBoxIcon.Warning); return; } // Perform secure erase using the selected pass sequence. bool result = CustomEraser.SecureErase(filePath, passSequence.ToArray(), CancellationToken.None); // Set the success flag if erase was successful. if (result) _SUCC = true; } |
Once the procedure described above has been implemented, it becomes essential to create a complementary function whose purpose is to evaluate the effectiveness of the selected sequence — whether it be the default one suggested by the algorithm or a custom sequence defined by the user. This step is crucial: by assessing how thoroughly each pattern contributes to data destruction, we ensure that the file erasure process meets the highest standards of security and reliability. Below is the procedure I’ve developed to perform this evaluation. It serves as a tool to measure, in real time, the robustness of the chosen overwrite pattern — offering both technical insight and valuable feedback to the user. Whether you're relying on the algorithm's default intelligence or exercising full manual control, this component guarantees transparency and confidence in the deletion process.
void Scorelist() { var items = listCustom.Items.Cast<string>(); // Create the evaluator's application var evaluator = new CustomPassEvaluator(items); // Evaluate the strength var result = evaluator.EvaluateStrength(); // Update UI progressBar1.Minimum = 0; progressBar1.Maximum = 100; progressBar1.Value = result.VisualValue; labScore.Text = result.StrengthLabel; } |
The procedures we've examined so far are essential for ensuring that my algorithm operates correctly and expresses its full potential. They lay the groundwork for a secure, efficient, and flexible file deletion process.
Now, let’s explore how to connect these core functions to the user interface — specifically, how to invoke them through the various buttons in your application.
We’ll see how to:
- Trigger the function that evaluates the strength and reliability of a given overwrite sequence,
- Call the method that suggests the best configuration according to Custom Erase’s logic,
- And finally, initiate the secure deletion process itself, applying the selected pattern sequence to the chosen file.
This stage is where the user interface and the algorithm come together — allowing end-users to experience the full power of secure, customizable deletion with just a few clicks.
After reviewing the core procedures essential for the proper functioning of the Custom Erase algorithm, it's time to see how to invoke them through button interactions within the interface.
The implementation is deliberately lightweight, straightforward, and designed to offer full control over the algorithm’s behavior — empowering developers to integrate secure deletion with minimal effort and maximum flexibility.
In the examples below, we’ll walk through two key scenarios:
- How to trigger the sequence suggested by Custom Erase, based on its built-in logic;
- How to launch the actual file deletion process, applying the selected overwrite pattern to the target file.
These actions mark the transition from configuration to execution, where the user’s choices — whether based on Custom Erase’s advice or fully customized — are translated into a precise and secure deletion routine.
As you can see, I’ve implemented the code within a button named btnSug. Naturally, you're free to name your buttons however you prefer, based on your own project’s naming conventions and architecture. In software development, consistent and meaningful naming plays an essential role in maintaining clean, readable, and scalable code. While I’ve chosen btnSug to indicate a button for suggesting an optimal sequence, you may adopt more descriptive or project-specific names such as btnGenerateSuggestion or btnRecommendPattern to better align with your overall coding style. The key is to ensure clarity and coherence across your interface elements and logic handlers. |
private void btnSug_Click(object sender, EventArgs e) { // Retrieve the suggested overwrite pattern sequence from the suggestion engine var suggestions = PassSuggestionEngine.GetSuggestedAlgorithm(); // Clear any existing items in the custom pattern list listCustom.Items.Clear(); // Populate the ListBox with the recommended overwrite patterns foreach (var suggestion in suggestions) { listCustom.Items.Add(suggestion); } // Calculate and display the effectiveness score of the selected sequence Scorelist(); } |
The code snippet you see here contains everything needed to invoke the secure deletion process in any context. Personally, I implemented an await Task.Run(() => procedure that operates under the control of a Timer.This approach allows the deletion process to run asynchronously without freezing the UI, ensuring a smooth user experience even during complex operations. You can examine the full implementation within the source code of the test project that accompanies my secure deletion algorithm. There, you’ll find how the timer and async logic are integrated to manage the process flow efficiently and responsively. |
_SUCC = false; // Reset success flag before starting the erase operation if (rdbCust1.Checked) { // Perform secure erase with a predefined sequence of passes bool success = CustomEraser.SecureErase(txtFilepathdel.Text, new[] { CustomPassType.Random, CustomPassType.Zeros, CustomPassType.Ones }); if (success) _SUCC = true; // Set success flag if operation succeeded } else if (rdbCust2.Checked) { // Call method that performs custom erase based on user selection CallCustomEraseFromListBox(); } |
As for the implementation and use of my secure data deletion algorithm within a project, that’s about everything you need to get started. As previously mentioned, you’ll find a complete example project included in the Source Code. This sample illustrates how to compile the DLL and integrate it into your own applications should you choose to adopt Custom Erase. The provided example serves as both a reference and a practical foundation, allowing you to experiment freely and tailor the integration to your specific development needs.
In this section, you can download the complete project to build a DLL that implements my secure deletion algorithm. The package includes the source code needed to create the DLL, the compiled DLL itself, and a sample application capable of securely deleting files of any type and size. Everything is provided with full transparency: the source code is included, along with hash verification files and my digital signature, ensuring the integrity and authenticity of the package. This solution is ideal for developers and security enthusiasts who wish to integrate reliable and verifiable file erasure functionality into their own applications.
# Custom Erase - Secure File Deletion Algorithm **Copyright (C) 2007–2025 Mariano Ortu** <https://www.sicurpas.it/> --- This algorithm is free software: you can redistribute it and/or modify it under the terms of the **GNU General Public License** as published by the Free Software Foundation, either **version 3 of the License**, or (**at your option**) any later version. This algorithm is distributed in the hope that it will be useful, but **WITHOUT ANY WARRANTY**; without even the implied warranty of **MERCHANTABILITY** or **FITNESS FOR A PARTICULAR PURPOSE**. See the [GNU General Public License](https://www.gnu.org/licenses/gpl-3.0.html) for more details. You should have received a copy of the GNU General Public License along with this class. If not, see: --- **SPDX-License-Identifier:** `GPL-3.0-or-later` |
Below you can download the complete Package, which includes the Source Code, the compiled DLL, the full projects needed to build the DLL itself, and a working example showing how to use my Custom Erase Algorithm. Everything is carefully organized and verified to offer a solid base for developers who wish to integrate secure deletion into their own applications, with full transparency and complete access to the underlying logic.
MD5 : 85E5BD32 9B331A9B 1E3AF26A 672B4E2A
SHA-1 : D4C0E581 F41833EB 0486A271 3662D8DC E9C74D56
SHA-256 : 7FB7CFD2 DE297CB1 A2AE4AD0 9D8CCC11 49013126
BB5C6154 4141BEFF 73FB4793
Size : 53248 B
Generated by EasyHash
-----BEGIN PGP SIGNATURE----- iQGzBAABCAAdFiEEb1LOBvdSdMY8vY6d/I6fuI4CcN8FAmhJjDwACgkQ/I6fuI4C cN9IswwAmlPMh1mM8zutkGq5MFZVtaR/GjpOU9JqJwHBsF31FvCLEtbSAgIcuu20 1ajvQhhlS6/3dVTpJw9f7DfxImsrwym4fv1E/VsvUUojNUyWOVGCG5vv3l7TVVHM +FOD6KUY9apgRgJZQ7roTqGd+eSxanK7bqoOtgX0v1G2aR68h1unyvgQJGLxs3ct 9U6h0psQ3O7dDw+U8W9B+Igk5QjBHh41rljusVJwL7S03GKr2UkaetPlraxdmOD8 /FRJRoIp6rAmbF9kddHrPQHtYe7KhHlTweVS/1HdcG12trBYurI7UFqtW/TvCy4g Hmc7ddbJC62MUcnAcWCHtPcSFrFlMHEiF0nH0HrfOZzvE9rNPXQKCp9p8hBbjUac UgQwro9h5zsbI5DwoNRMsRQ8naF8Yd6EX65Eqhu6waquQvY6xRUhem+GcgBMKBN+ vZ2Ray3WvY0XnLYPIZgxpxMtiGSGnZRZ6/SYeCu3v8tx/DeFrXBO1osmzHEjrQdS V9gIwgDq =N9+K -----END PGP SIGNATURE----- |
MD5 : C6840CD8 45B37114 20DA7817 84889191
SHA-1 : 8EA7C0BE F5FA81E3 6AC13BF7 2D65CF90 C591CEAE
SHA-256 : B20A5636 F6060914 A887F2B6 0E4A2BF6 F20925D0
7123CA30 B45A9A8E 43DCCA80
Size : 8192 B
Generated by EasyHash
-----BEGIN PGP SIGNATURE----- iQGzBAABCAAdFiEEb1LOBvdSdMY8vY6d/I6fuI4CcN8FAmhJjE8ACgkQ/I6fuI4C cN9ktAwAjo8yIL3QNf4DAQHBYdM+KQcbP/CGweVE6yaREmpkDeNEn4PHzTvG6c14 4wMRAEYRW9EWMVFQgE9DVPbl3Mkuvz0MYFtsDY6ZKJnSL/UQcuQNyNmUmzFJWi65 nGuDE2vfATmrzioBYhsp+/wtbErFoz32MXZUgbt0XUPYsgtPqaBD/i+dYv8nYe7G l0E+G9JisR3KvlcMzWQ/Pt6KKQuMfM8iWeT3H3zZFVt1QYPv1X4OTBybL/OOLySy mzoIxInVbW3PotsKUGnqatkiLg3HxCuij3kdqPDRlNODbfp1/IVTJJkC3+SGsNHE XgLkTOOdBU5dZ9kbfOtpKH//9iDH4rj1CBMCYlQLVH30gzJIoJGL26qEfLO2Cj7k T1EyprOh4+qa67OibZtoyx9DM/U+j6BHMXYSjcJL7thnDO3ZCsQ+EsiBfG3ape4D TQve7dwaM5M9etSYZpVY9WfaXGFylWUiChbhApvHf3vxnAVXUCsDnz5HmBl5awDT IrmXMT3N =2J0m -----END PGP SIGNATURE----- |
MD5 : 05406F89 E0F8819D F7C85C31 05AA1F9B
SHA-1 : 0ACE6B2D 0E96E27C 76519EBA FE5278E7 CEF4CE9D
SHA-256 : 6E501DF8 73CA47C7 E1C7B822 3CD0A9B2 8B7F9B9E
35C42AFF 5EF88806 D39E0B78
Size : 102400 B
Generated by EasyHash
-----BEGIN PGP SIGNATURE----- iQGzBAABCAAdFiEEb1LOBvdSdMY8vY6d/I6fuI4CcN8FAmhJjGYACgkQ/I6fuI4C cN/A2Qv+I8/l4CDGSdUVXruvfPouTEdYtTrfrtu686N8bUXNdKu2ZaBKMvlDTtXE GnIKL5ccrRK4okfK3uU8LZYojOBuuCE7K0CvaQGXkNu2JbaKsmlP928LK614QA4z MtMdQZDowI677T4/JL1C68OODJW1cgNLiFeVh3fo7GWtw3mDiHpUY5rlAU3vLFB9 8EkMGvCgeFOv0n584Dk0l/Ws+zWqxm4/zpBZF87w/SKOoQYeXhK8TBKD46RD1rOe 5lVo/48uF5MzE0U0t6Ieaf4nhyOBorSSIx6nSbrpn+fvBoLW+CYii1PyVlobusHI qsUjA/s2dODPVGTPpseFre2cWWGI2fXuiE85ZbtiPhHDDkina7b/MSndI8UOgcW2 KP7oparwTQIs50pmrjGcT5N73VNb49c8B2Cu4N3O5rvl0KK1Y5YChNxuuVXHwhNn uUx+x855aseF/aTrHU17bzXp3UjPNl9B/rDuG3FF2yILT4dimTXIDJxXiknX3n/X qqeN5Qly =po4x -----END PGP SIGNATURE----- |
The Package includes the CustomEraser Project, the CustomTest Demo, and the compiled DLL
CustomEraser.dll. Each individual .zip archive is digitally signed, ensuring that users can safely download and verify the authenticity of every file. You can access and download the entire Package directly from my Official GitHub Repository!This repository provides a complete and secure solution for integrating CustomEraser, a powerful algorithm designed for irreversible and responsible file deletion. Feel free to explore the code, run the test application, and use the DLL in your own secure software solutions.
In this section, you can find a short guide in Italian that describes the technical features of the Custom Erase Algorithm. The file is in PDF Format and can be downloaded directly to your PC. The Italian-language guide was created by one of my closest collaborators, Stefano Scarpello. Thanks Stefano!















